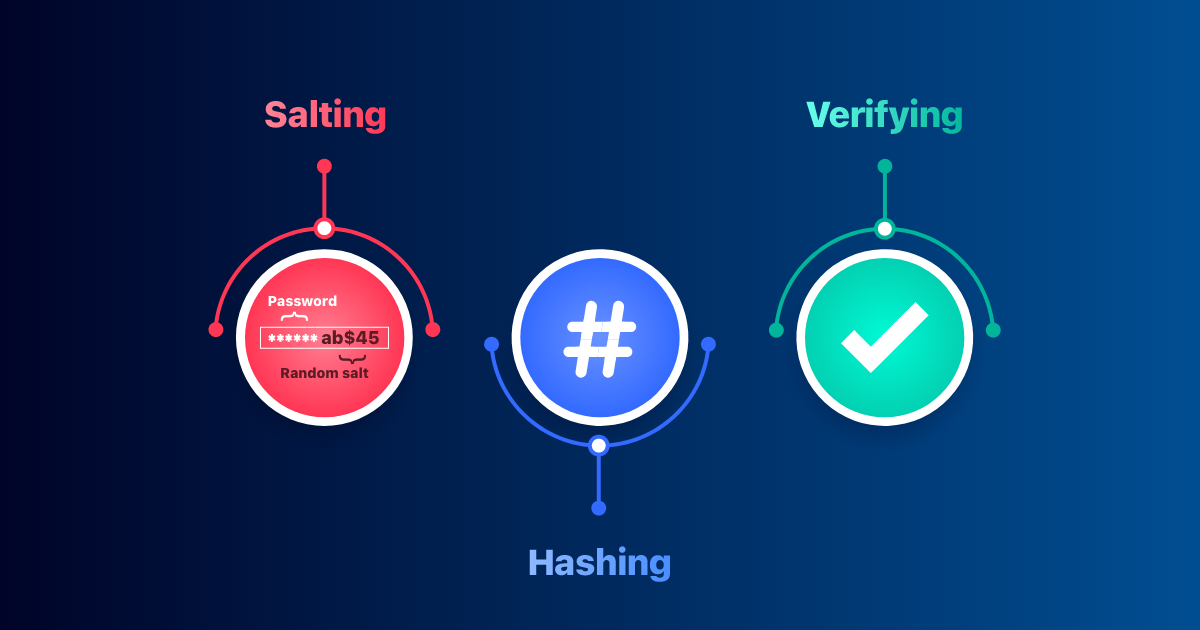
Passwords and hacking: the jargon of hashing, salting and SHA-2 explained | Data and computer security | The Guardian
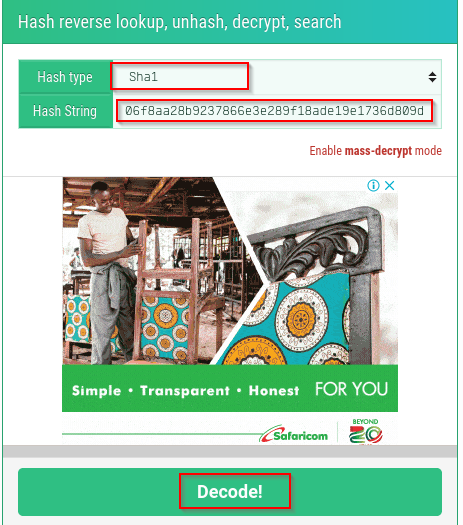
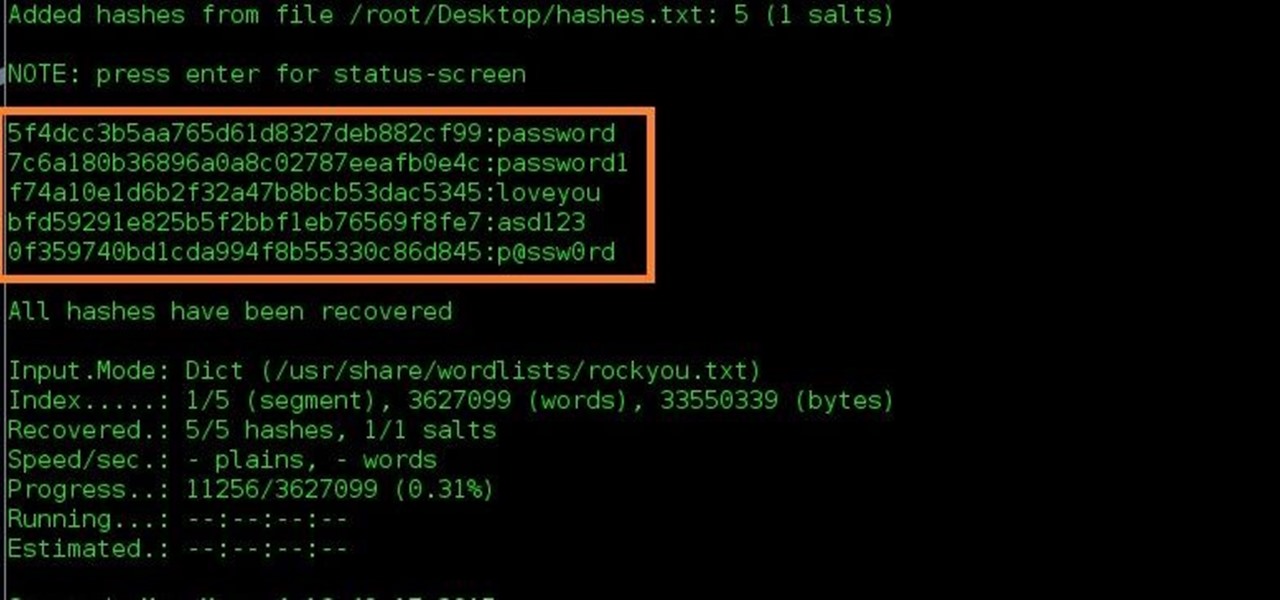
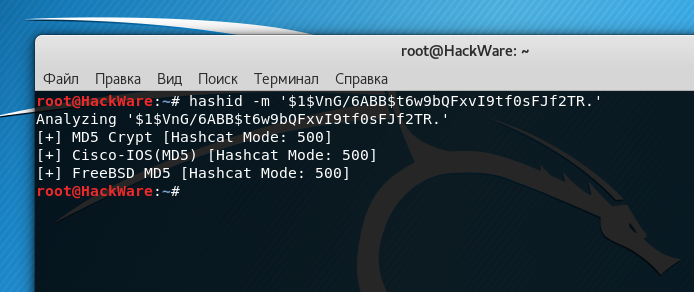
Challenge Description A hacker leaked the below hash online.Can you crack it to know the password of the CEO? the flag is the password Hash:06f8aa28b9237866e3e289f18ade19e1736d809d First go to hash… - arnold sydney -




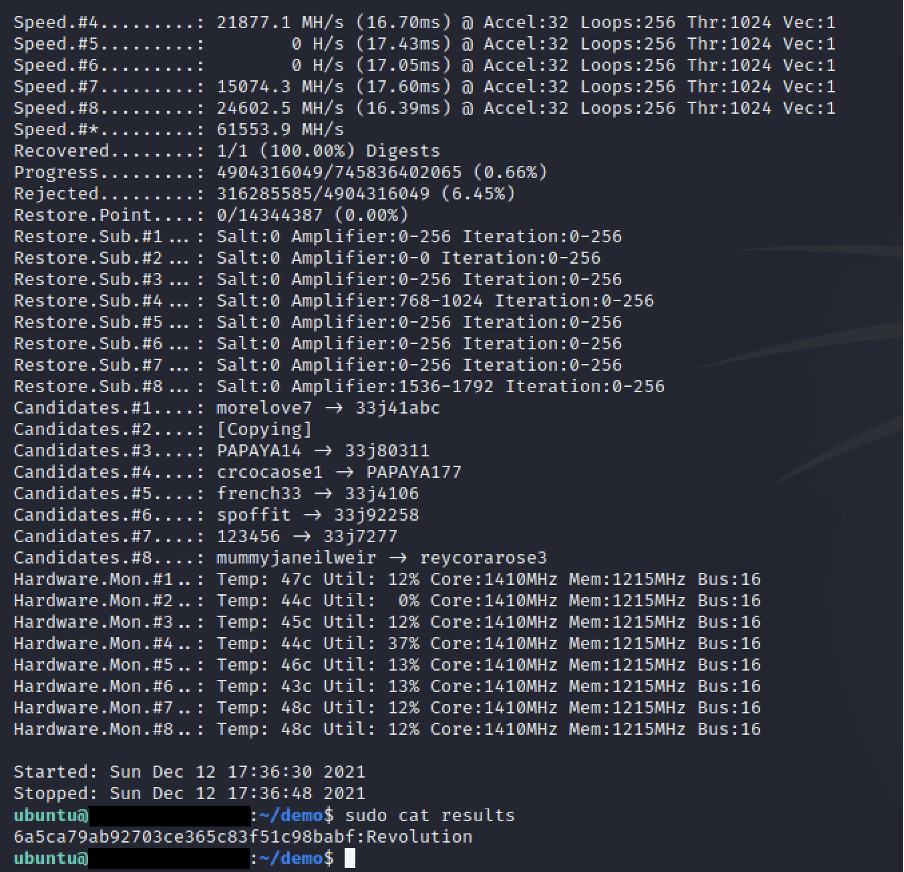


![hashcat [hashcat wiki] hashcat [hashcat wiki]](https://hashcat.net/wiki/lib/exe/fetch.php?tok=505d08&media=https%3A%2F%2Fhashcat.net%2Fhashcat%2Fhashcat.png)
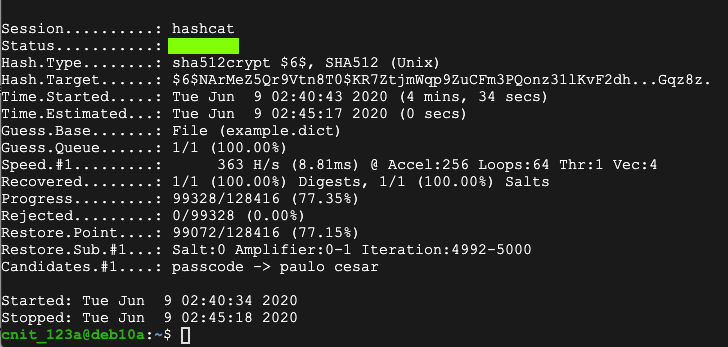

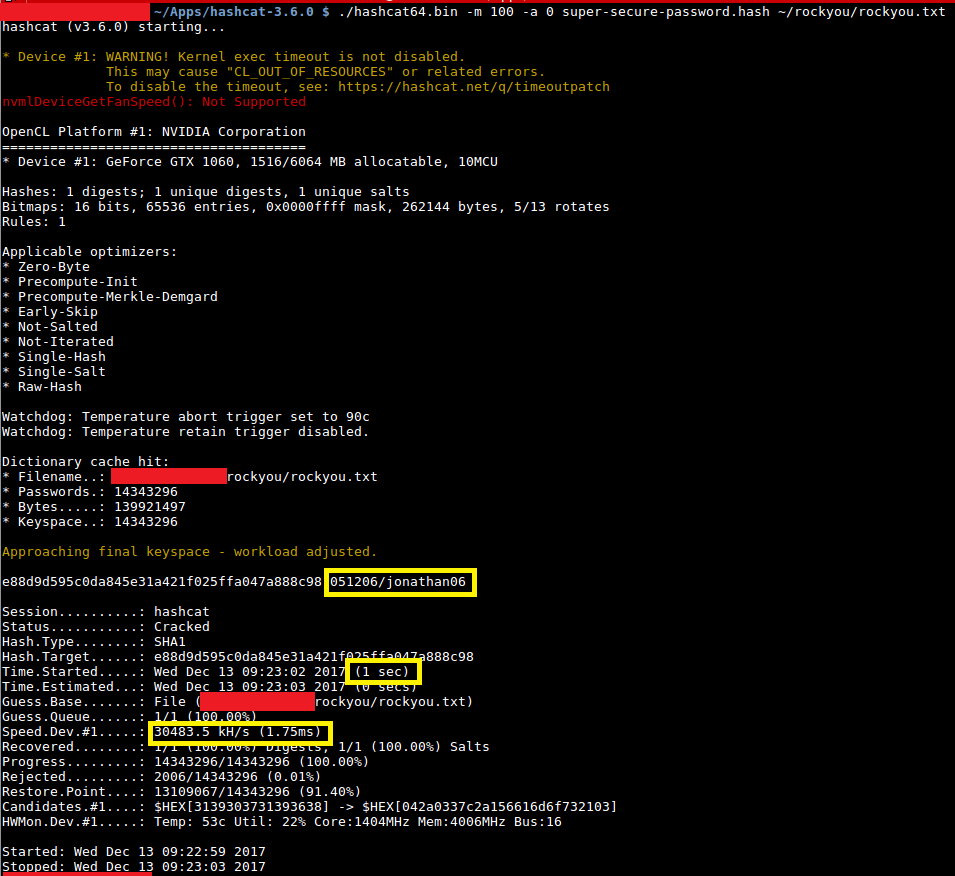

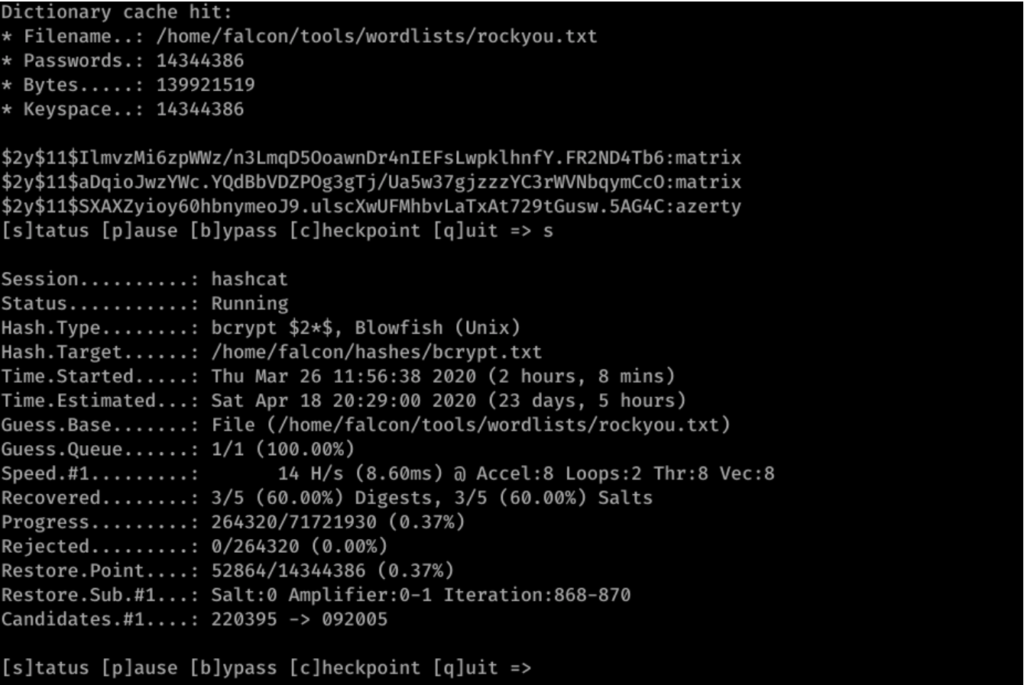

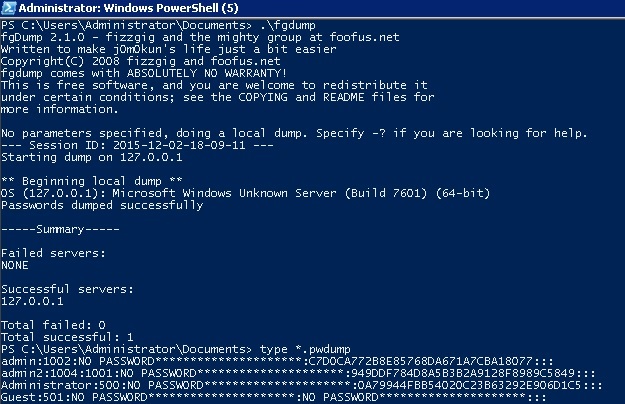
![Hashcat tutorial for beginners [updated 2021] | Infosec Resources Hashcat tutorial for beginners [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/2018/04/122120-2.png)